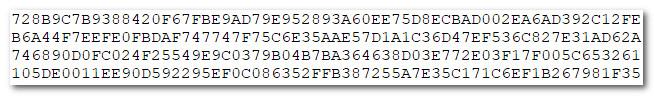
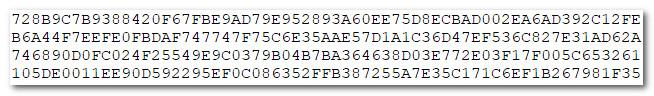
dim as longint m=123456789, n=31,r
asm
movq xmm2,[n]
movq xmm3,[m]
pand xmm3, xmm2
movq [r],xmm3
end asm
? r,m and n
asm
movq xmm2,[n]
movq xmm3,[m]
pand xmm3, xmm2
movq [r],xmm3
end asm
? r,m and n

Encrypternet is a small utility for encrypting files in such a way that they may be safely sent over the Internet or downloaded from a website.
The minimum operating system requirement is Windows Vista. Encrypternet uses Microsoft Windows functions that are not available in older platforms.
The core component of Encrypternet uses the Advanced Encryption Standard (AES) employing the Cipher Block Chaining (CBC) mode of operation. There are three variants, 128-bit, 192-bit and 256-bit. The National Institute of Standards and Technology (NIST) clearance levels are 128 bits up to Secret and 192/256 bits up to Top Secret. The target audience for Encrypternet is for those requiring confidentiality up to Secret so AES-128 is used. AES is a symmetric algorithm where the same password is used for both encryption and decryption. When encrypting locally for our own purposes we could store our password in our head, in a wallet, in a password manager or wherever. Sending an encrypted file over the Internet poses the problem of getting a password safely to a receiver. Encrypternet does not require a user supplied password, it generates one itself and neither the sender nor receiver actually see it.
Encrypternet uses public key encryption: It generates a 128-bit random binary key giving then a 16 byte 'password'. The bytes have random values between 0 and 255. The key then is not readable as would be with a textural password. The binary key is then encrypted using a receiver's RSA public key. RSA is very slow compared with AES and is limited to the amount of data it can encrypt. However, it is ideal for encrypting passwords. The NIST reckon that RSA-2048 should hold us in good stead until about 2030 beyond which we should move up 3072 bits. However, Encrypternet uses RSA-3072 because that has a security strength of 128 bits; the same as AES-128. The sender never sees the 'password' and it is very unlikely to be used again. Our receiver uses their RSA-3072 private key to decrypt the encrypted 'password' using their copy of Encrypternet and they never see the 'password' either.
When sending encrypted files over the Internet or downloading them from a website the encryption should be authenticated. There are many ways of doing this as well but Encrypternet uses a Digital Signature Algorithm (DSA) and, in particular, an Elliptic Curve Digital Signature Algorithm (ECDSA). When the AES encryption has completed a secure hash is determined on the encrypted data. A hash is a digest. It is a bit like compression but produces a value of the same length no matter what the size of the encrypted data is. Encrypternet uses the hash algorithm SHA256 which also has a security strength of 128 bits. It is extemely unlikely that the value will be the same for different data. The hash is then digitally signed with the sender's ECDSA private key. An attacker could alter the AES encrypted data and calculate a new hash but they would not be able to sign it without the sender's ECDSA private key. Encrypternet uses ECDSA-256 because that also has a security strength of 128 bits. Our receiver uses the sender's ECDSA public key to verify the hash and then compares the sent hash with a hash of the encrypted data. If everything goes to plan the decrypted 'password' is then used to decrypt the encrypted data.
There is a method of hashing called HMAC which is a hash with a password. An attacker could change a hash but it would be no good without the correct password. There is a difference between using a HMAC and a DSA. HMAC is symmetrical - both the sender and receiver use the same password. Digital Signatures are asymmetric and provide integrity plus non-repudiation whereas HMAC provides only integrity. The sender then cannot repudiate the signature as their private key is not known to anyone else.
So, Encrypternet uses AES, RSA, SHA256 and ECDSA and all with a security strength of 128 bits. Encrypternet then has a security strength of 128 bits.
On the face of it, it would seem that we are generating a lot of files: Encrypted data, encrypted password, hash and signature. Encrypternet puts them all into a single file, which we call an Encrypternet package, and that is sent to the receiver. The receiver uses their copy of Encrypternet and all the various components are extracted to finally give them a decrypted/plaintext file.
If you have Windows 7 or later and your CPU supports AES-NI then the encryption is done via hardware otherwise the Windows software functions are used.
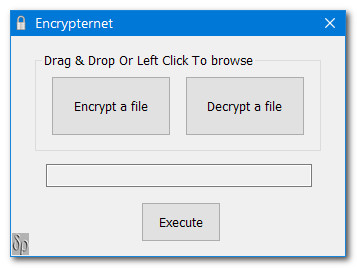
Here is Encrypternet's form:-
The minimum operating system requirement is Windows Vista. Encrypternet uses Microsoft Windows functions that are not available in older platforms.
The core component of Encrypternet uses the Advanced Encryption Standard (AES) employing the Cipher Block Chaining (CBC) mode of operation. There are three variants, 128-bit, 192-bit and 256-bit. The National Institute of Standards and Technology (NIST) clearance levels are 128 bits up to Secret and 192/256 bits up to Top Secret. The target audience for Encrypternet is for those requiring confidentiality up to Secret so AES-128 is used. AES is a symmetric algorithm where the same password is used for both encryption and decryption. When encrypting locally for our own purposes we could store our password in our head, in a wallet, in a password manager or wherever. Sending an encrypted file over the Internet poses the problem of getting a password safely to a receiver. Encrypternet does not require a user supplied password, it generates one itself and neither the sender nor receiver actually see it.
Encrypternet uses public key encryption: It generates a 128-bit random binary key giving then a 16 byte 'password'. The bytes have random values between 0 and 255. The key then is not readable as would be with a textural password. The binary key is then encrypted using a receiver's RSA public key. RSA is very slow compared with AES and is limited to the amount of data it can encrypt. However, it is ideal for encrypting passwords. The NIST reckon that RSA-2048 should hold us in good stead until about 2030 beyond which we should move up 3072 bits. However, Encrypternet uses RSA-3072 because that has a security strength of 128 bits; the same as AES-128. The sender never sees the 'password' and it is very unlikely to be used again. Our receiver uses their RSA-3072 private key to decrypt the encrypted 'password' using their copy of Encrypternet and they never see the 'password' either.
When sending encrypted files over the Internet or downloading them from a website the encryption should be authenticated. There are many ways of doing this as well but Encrypternet uses a Digital Signature Algorithm (DSA) and, in particular, an Elliptic Curve Digital Signature Algorithm (ECDSA). When the AES encryption has completed a secure hash is determined on the encrypted data. A hash is a digest. It is a bit like compression but produces a value of the same length no matter what the size of the encrypted data is. Encrypternet uses the hash algorithm SHA256 which also has a security strength of 128 bits. It is extemely unlikely that the value will be the same for different data. The hash is then digitally signed with the sender's ECDSA private key. An attacker could alter the AES encrypted data and calculate a new hash but they would not be able to sign it without the sender's ECDSA private key. Encrypternet uses ECDSA-256 because that also has a security strength of 128 bits. Our receiver uses the sender's ECDSA public key to verify the hash and then compares the sent hash with a hash of the encrypted data. If everything goes to plan the decrypted 'password' is then used to decrypt the encrypted data.
There is a method of hashing called HMAC which is a hash with a password. An attacker could change a hash but it would be no good without the correct password. There is a difference between using a HMAC and a DSA. HMAC is symmetrical - both the sender and receiver use the same password. Digital Signatures are asymmetric and provide integrity plus non-repudiation whereas HMAC provides only integrity. The sender then cannot repudiate the signature as their private key is not known to anyone else.
So, Encrypternet uses AES, RSA, SHA256 and ECDSA and all with a security strength of 128 bits. Encrypternet then has a security strength of 128 bits.
On the face of it, it would seem that we are generating a lot of files: Encrypted data, encrypted password, hash and signature. Encrypternet puts them all into a single file, which we call an Encrypternet package, and that is sent to the receiver. The receiver uses their copy of Encrypternet and all the various components are extracted to finally give them a decrypted/plaintext file.
If you have Windows 7 or later and your CPU supports AES-NI then the encryption is done via hardware otherwise the Windows software functions are used.
Here is Encrypternet's form:-
ENCRYPTERNET
For encryption we either drag & drop a target file onto 'Encrypt a file' or left click on 'Encrypt a file' and browse. With decryption we use the 'Decrypt a file' button. In both cases the target file is displayed in the blank text box. With encryption an open file dialog is displayed so that we can browse for a RSA public key. On decryption an open file dialog is displayed so that we can browse for an ECDSA public key. If the keys are kept in the same folder as Encrypternet then we will not have to browse; we simply choose from the displayed list. To keep things simple and secure we have put the Encrypternet folder onto a flash drive and insert it as when we need to. The Encrypternet folder could, of course, be put onto a local HDD or SSD but we would suggest that your private keys be placed on removeable media. Encrypternet will first look into the Encrypternet folder for private keys and if not found an open file dialog will open inviting us to browse for them.
Encrypternet may be used for home encryption. In this case we are both the sender and the receiver. If the keys are kept in the same folder as Encrypternet then execution will commence immediately after selecting a target file.
So, where do we get our keys from? In the download there is an application called GenerateKeyPairs. On execution a RSAPrivateKey.dat, RSAPublicKey.dat, ECDSAPrivateKey.dat and ECDSAPublicKey.dat are created. Their names should not be changed. If we get, say, Bob's public keys then we could rename them as BobRSAPublicKey and BobECDSAPublicKey and they are best placed in the Encrypternet folder. The open file dialog, on encryption, for example, will display files matching the filter *RSAPublicKey* so we can either prepend/append or both for a receiver's RSAPublicKey. Similarly for a ECDSAPublicKey.
Encrypternet may seem a little draconian as a sender will create a package for a single receiver. However, an employee in Washington, DC, for example, could send a package to an employee in Seattle who has been designated the Seatle's decryptor. If the encrypted data is meant for a small group of employees in Seattle the Seattle decryptor could then decrypt the package and then send the plaintext or encrypt it locally, using a simpler encryption protocol, for only that small group of employees. The package could be sent via email or uploaded to a website for the Seattle's decryptor to download. A lot of people work from home nowadays rather than an office. Indeed, they may live hundreds of miles from their office. For the office to send confidential data to an employee and vice versa then the 'sender/single receiver' aspect of Encrypternet is ideal.
The download has two versions of Encrypternet and GenerateKeyPairs: 32-bit and 64-bit. If your version of Windows is 64-bit then choose that - the encryption has pretty much the same speed for both but decryption is a little faster with the 64-bit version. In both cases the decryption is already faster than encryption because the SHA256 hash and the decryption are executed asynchronously.
We can encrypt/decrypt very large files because they are 'streamed' in via a 256KB buffer. Encrypternet then does not use a lot of RAM.
The download also has a chm Help file and a License in the main Encrypternet folder.
Please read the License before using the software. If you use the software it will be assumed that you have read the License.
If you want to get in touch click on the deltarho icon at the top left of the web page. Needless to say if you spot any bugs then please let me know.
Encrypternet is freeware but you may make a donation by clicking on the button below.
David Roberts
Encrypternet may be used for home encryption. In this case we are both the sender and the receiver. If the keys are kept in the same folder as Encrypternet then execution will commence immediately after selecting a target file.
So, where do we get our keys from? In the download there is an application called GenerateKeyPairs. On execution a RSAPrivateKey.dat, RSAPublicKey.dat, ECDSAPrivateKey.dat and ECDSAPublicKey.dat are created. Their names should not be changed. If we get, say, Bob's public keys then we could rename them as BobRSAPublicKey and BobECDSAPublicKey and they are best placed in the Encrypternet folder. The open file dialog, on encryption, for example, will display files matching the filter *RSAPublicKey* so we can either prepend/append or both for a receiver's RSAPublicKey. Similarly for a ECDSAPublicKey.
Encrypternet may seem a little draconian as a sender will create a package for a single receiver. However, an employee in Washington, DC, for example, could send a package to an employee in Seattle who has been designated the Seatle's decryptor. If the encrypted data is meant for a small group of employees in Seattle the Seattle decryptor could then decrypt the package and then send the plaintext or encrypt it locally, using a simpler encryption protocol, for only that small group of employees. The package could be sent via email or uploaded to a website for the Seattle's decryptor to download. A lot of people work from home nowadays rather than an office. Indeed, they may live hundreds of miles from their office. For the office to send confidential data to an employee and vice versa then the 'sender/single receiver' aspect of Encrypternet is ideal.
The download has two versions of Encrypternet and GenerateKeyPairs: 32-bit and 64-bit. If your version of Windows is 64-bit then choose that - the encryption has pretty much the same speed for both but decryption is a little faster with the 64-bit version. In both cases the decryption is already faster than encryption because the SHA256 hash and the decryption are executed asynchronously.
We can encrypt/decrypt very large files because they are 'streamed' in via a 256KB buffer. Encrypternet then does not use a lot of RAM.
The download also has a chm Help file and a License in the main Encrypternet folder.
Please read the License before using the software. If you use the software it will be assumed that you have read the License.
If you want to get in touch click on the deltarho icon at the top left of the web page. Needless to say if you spot any bugs then please let me know.
Encrypternet is freeware but you may make a donation by clicking on the button below.
David Roberts
Copyright © 2018-2021 David Roberts. All Rights Reserved.